HoneyDoc
Cutting-edge privacy & security reporting tool
Besides its zero-trust architecture, HoneyDoc simplifies reporting & management for your team.
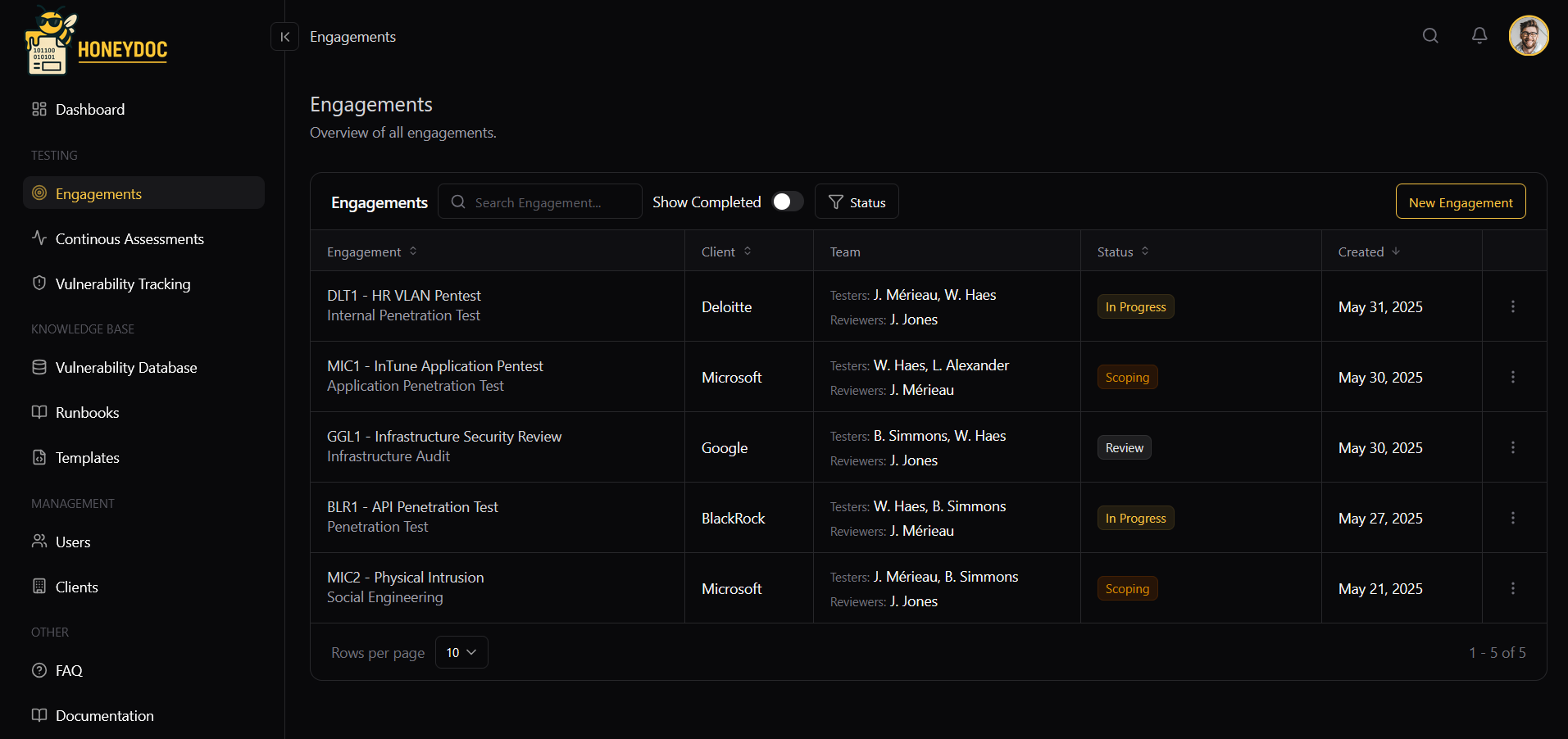
Core Concept
Secure pentest reporting
made simple
HoneyDoc is a zero-trust platform designed by pentesters for pentesters, combining robust security with intuitive project management.
Built on a zero-access encryption model, all data is encrypted in your browser before reaching the server. With zero-knowledge authentication, even a complete breach of the infrastructure cannot compromise your sensitive reports and findings. Deploy anywhere - public cloud, private network, or air-gapped environment - the browser-first security model ensures your data stays protected regardless of the server and hosting location.
Zero-Trust Security
End-to-end encryption with client-side key management ensures your data remains private even if our servers are compromised.
Team Collaboration
Real-time collaboration with granular access control, perfect for both pentesters and project managers.
Smart Templates
Customizable report templates with built-in vulnerability database, CWE mappings, and risk matrices.
Project Tracking
Comprehensive project management with scheduling, resource allocation, and progress monitoring.
Complete Pentest Reporting Suite
Everything you need for efficient and secure pentest management
Vulnerability Management
Built-in vulnerability database with CWE & OWASP mappings. Import findings from Nessus, Nmap and other tools. Track vulnerabilities across projects with powerful analytics.
Advanced Collaboration
Real-time collaboration with QA comments, phased testing support, and retest tracking. Perfect for team coordination and client communication.
Documents
Generate various document types - pentest attestations, executive presentations, technical reports. Track deliverable history with version control.
Runbooks & Documentation
Create and manage detailed runbooks for standardized testing procedures. Secure file storage for evidence and documentation with zero-access encryption.
Risk Assessment
Built-in risk matrix for accurate threat modeling. Track and analyze security metrics across projects with detailed analytics dashboards.
Project Management
Comprehensive scheduling and resource management. Track project phases, retests, and team workload with intuitive dashboards.
Security Measures
Continuous monitoring of cryptographic keys and frontend integrity. Automatic alerts for suspicious activities and tampering attempts.
AI Report Writing
Optional AI assistance for report writing and formatting. Configure your own LLM API for complete control over data processing and privacy.
Flexible Deployment
Deploy anywhere - cloud, private network, or air-gapped environment. Browser-based security ensures data protection regardless of hosting.
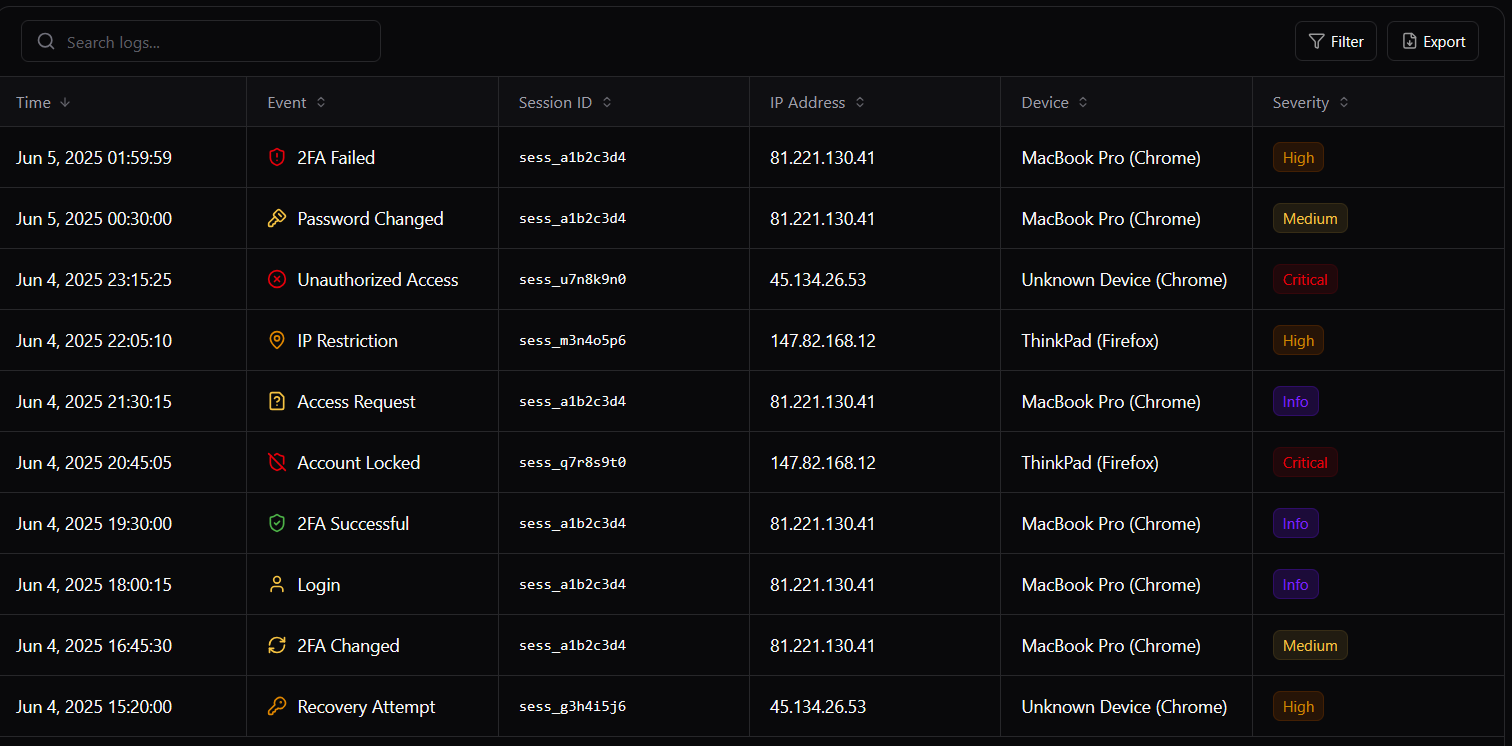
Keep your data safe
Security alerts & logs
Request-based access
Access to projects requires explicit approval from existing members who share encryption keys, ensuring complete control over who can view sensitive data.
Smart device monitoring
Our trust scoring system tracks device behavior and access patterns, automatically alerting managers and blocking access when suspicious activity is detected.
Granular access control
Define precise access rules based on time windows, geographic locations, and IP addresses to maintain tight security while enabling legitimate access.
Solutions comparison
We have nothing to envy
HoneyDoc
Zero-trust platform with complete workflow
Core Features
Advanced Features
Deployment & Security
Competitor Comparison
See how HoneyDoc compares to other solutions
Available Features
Limited Support
Missing Features
Available Features
Limited Support
Missing Features
Available Features
Missing Features
Available Features
Missing Features
| Reporting Solutions |
HoneyDoc Zero-trust platform Complete workflow, higher security |
PwnDoc Open-source solution Basic features, limited tracking |
Sysreptor Hybrid licensing model Good reports, basic workflow |
PlexTrac Enterprise platform Full features, complex setup |
AttackForge Enterprise platform Rich features, steep learning |
|---|---|---|---|---|---|
| Vuln. DB | |||||
| Phases | |||||
| Retests | |||||
| Vuln. tracking | |||||
| Collaborative | |||||
| QA comments | |||||
| Runbooks | |||||
| File storage | |||||
| CWE & OWASP DB | |||||
| Analytics | |||||
| Scheduling | |||||
| Ingestion (Nessus, nmap...) | |||||
| Max. users | Unlimited | Unlimited | License based | License based | License based |
| Self hosting | License based | License based | |||
| Multi-types (PPT, XLS...) | |||||
| Deliverables history | |||||
| Risk matrix | |||||
| Artificial Intelligence | |||||
| Zero-knowledge authentication | |||||
| Zero-access encryption |
HoneyDoc is
HoneyDoc will saves your team tons of time, it is easy to customize and is the most secure reporting solution available.
Ask for a demo
Contact usDo you have questions?
Here are answers to common questions about HoneyDoc's security model and features.
Need more details? Feel free to reach out!
We use OPAQUE, a modern password authentication protocol that ensures your password never leaves your device. Here's how it works:
- Your password is transformed into a secure key on your device
- Only this transformed key is used to authenticate with the server
- Even if our servers are breached, attackers can't recover your password or impersonate you
- The server never sees or stores your actual password
Think of it like a high-tech lock where you keep the only key, and the server only knows how to verify if the key is correct without ever seeing it.
We use XChaCha20-Poly1305 encryption and X25519 keys to ensure only authorized team members can access sensitive data. Here's what this means:
- All sensitive data is encrypted in your browser before it reaches the server
- Each team member has their own unique key pair for accessing shared data
- Even the server, cannot read the data
- The encryption is so strong it would take supercomputers millions of years to break
Imagine having a vault where each document is locked in an unbreakable box, and only authorized team members have the keys to open them. The server just stores these locked boxes without any ability to peek inside.
Yes! Thanks to our browser-first security model, you can host HoneyDoc anywhere:
- Your own infrastructure or private cloud
- Air-gapped environments for maximum isolation
- Local network for internal use only
Since all security measures happen in your browser, the hosting location doesn't affect the security of your data.
Our encryption system is optimized for real-world use:
- Documents open instantly for most sizes
- Large files (100MB+) decrypt in seconds
- Bulk operations are processed in parallel
- Everything happens locally in your browser for maximum speed
Modern browsers are incredibly fast at encryption operations, so you won't notice any delay in your daily work.
We've designed the system with backup access in mind:
- Administrators can reassign access to projects
- During registration, users receive a recovery key that should be securely stored offline
This ensures you can always regain access to your data in case of emergency.
Yes! We've designed HoneyDoc with usability in mind:
- Intuitive interface designed by pentesters for pentesters
- All security happens behind the scenes
- Built-in templates and automation save time
- Comprehensive but easy-to-navigate dashboard
You get enterprise-grade security without compromising on user experience.
HoneyDoc works with all modern browsers that support the Web Crypto API:
- Chrome, Firefox, Safari, and Edge (latest versions)
- Both desktop and mobile browsers are supported
- No plugins or extensions required
- All cryptographic operations use native browser capabilities
We recommend using the latest version of your preferred browser for the best performance and security.
Our security model helps meet strict compliance requirements:
- Zero-access encryption exceeds most data protection standards
- Detailed security logs for user actions
- Self-hosting option for data sovereignty
- Configurable retention policies
The browser-based security model ensures your data handling aligns with regulations like GDPR, HIPAA, and others.
Ready for a demo?